Compliance management software for ISO 27001
Stay Compliant to ISO 27001 Requirements with EventLog Analyzer
ISO 27001 is the international standard for securing your information assets from threats. It is the best-known standard that provides precise requirements for a holistic information security management.
ISO 27001 standard will help your organization manage the security of sensitive assets such as financial data, intellectual property, employee records, customer data, and other sensitive information. It mandates that enterprises enforce information security, thereby reducing the possible risk of data thefts and breaches.
EventLog Analyzer can make your organization to comply with the ISO 27001:2013 controls A.12.4.1, A.12.4.2 and A.12.4.3, These controls help organizations to record events and generate evidence. EventLog Analyzer also fulfills the controls A.9.2.1, A.9.2.5 and A.9.4.2 that ensures authorized user access and prevents unauthorized access to systems and services.

| Requirement Number |
Requirement Description |
How EventLog Analyzer fulfills the requirement? |
A.12.4.1
Event logging |
Event logs recording user activities; exceptions, faults and information security events shall be produced, kept and regularly reviewed. |
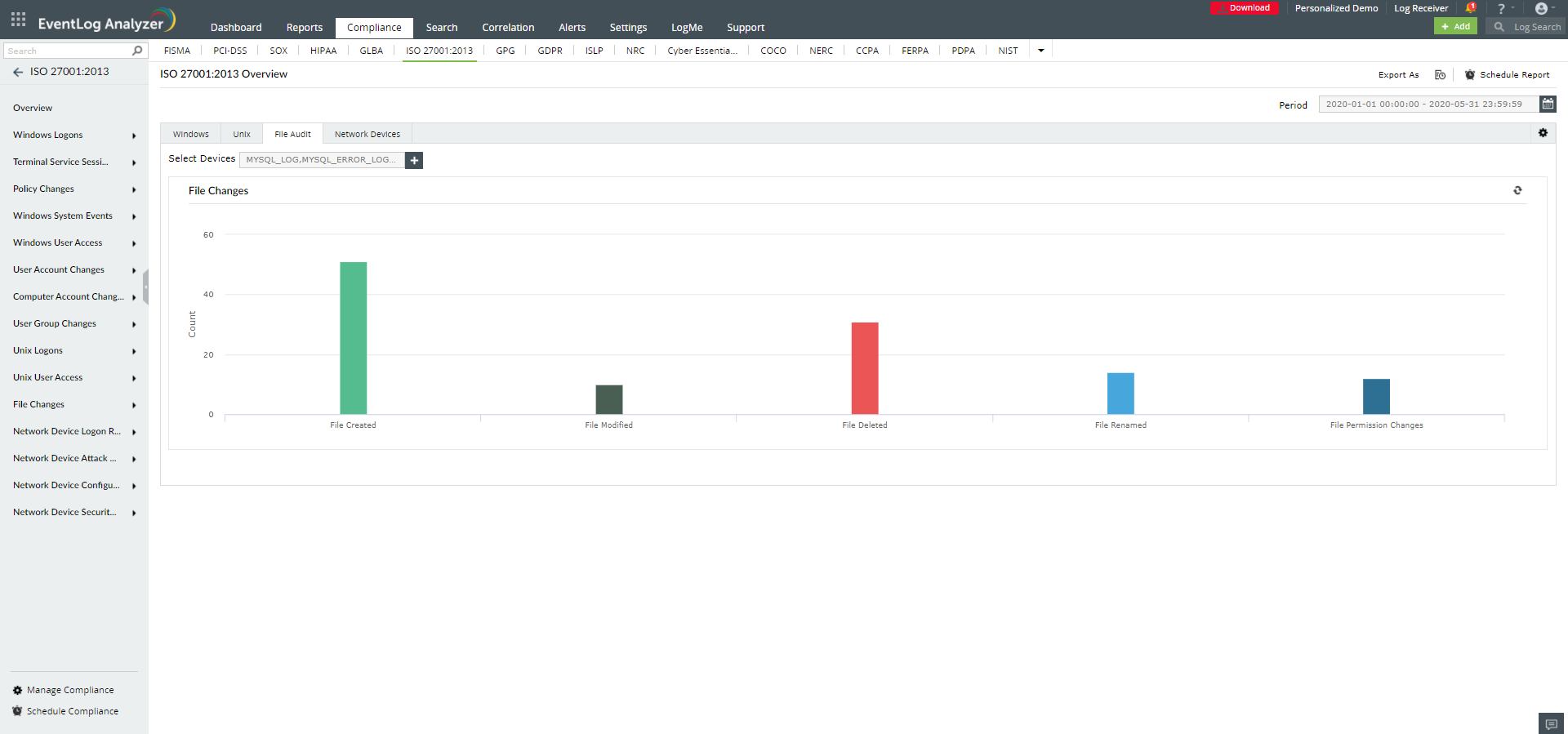
EventLog Analyzer software enables organizations to completely automate the entire process of managing terabytes of logs by collecting, analyzing, searching, reporting, and archiving it in a central location. It archives all log data on the EventLog Analyzer server itself.
All user activities, server activities, errors, security events, information events, application events, and other events are monitored and analyzed by EventLog Analyzer in real-time.
All the critical security events such as user activities, server activities, errors, and other events such as information events, and application events are monitored and analyzed by EventLog Analyzer in real-time. The solution also reviews all the above said events regularly with its out-of-the-box reports. |
A.12.4.2
Protection of log information |
Logging facilities and log information shall be protected against tampering and unauthorized access. |
EventLog Analyzer encrypts the event log archive files to ensure the log data is secured for future forensic analysis, compliance and internal audits by hashing and time stamping the log data.
The solution also securely stores the archived log data files by employing hashing and time stamping techniques. The time stamping technique ensures that the archive data files are tamper proof. If there is a modification, in the archived log file, then this technique will reveal that the file had been tampered.
EventLog Analyzer’s object access monitoring and File Integrity Monitoring capability ensures that the log information is kept secured from all threats. |
A.12.4.3
Administrator and operator logs |
System administrator and system operator activities shall be logged and the logs protected and regularly reviewed. |
EventLog Analyzer provides you with PUMA (Privileged user monitoring and audit) reports. The solution closely monitors the user activity of system administrators and operators and gives you detailed security reports for any specific period of time. The graphical reports give the complete picture of user activities and also allow you to drill down to the level of raw logs which give in-depth security insights. You can also export the reports in PDF and CSV formats.
EventLog Analyzer captures all user audit trails to ensure that the log files that capture the activities of system administrators and system operators are protected from unauthorized access and threats.
EventLog Analyzer monitors and analyzes important log events such as User Logons, User Logoffs, Failed Logons, Successful User Account Validation, Failed User Account Validation, Audit Logs Cleared, Audit Policy Changes, Objects Accessed, User Account Changes, User Group Change and more. |
A.9.2.5
Review of user access rights |
Asset owners shall review users access rights at regular intervals. |
EventLog Analyzer generates security reports that can tell you the list of devices generating maximum number of successful and failed login events.
Monitoring the login events in real-time will allow asset owners to know when their network is vulnerable to security threats.
|
A.9.4.2
Secure log-on procedures |
Where required by the access control policy, access to systems and applications should be controlled by a secure log-on procedure. |
EventLog Analyzer collects and generates reports on all account management and account usage activity events. Changes to accounts, user policies, domain policies, and audit policies are monitored, analyzed, and reports are generated in real-time.
The solution monitors and analyzes in real time, user access events related to access and authorization of critical systems, devices, and applications. It also monitors and tracks the security level permission change events as well. |
9.2.1
User registration and de-registration |
A formal user registration and de-registration process should be implemented to enable assignment of access rights. |
EventLog Analyzer generates detailed reports and alerts you in real-time upon the occurrence of new user account creation, deletion and modification, across your network. The solution also sends out Email/SMS alerts when a user account is locked out. |
Sail through audits for ISO 27001.
Thanks!
Your download is in progress and it will be completed in just a few seconds!
If you face any issues, download manually here
Other features
Comply with the stringent requirements of regulatory mandates viz., PCI DSS, FISMA, HIPAA, and more with predefined reports & alerts. Customize existing reports or build new reports to meet internal security needs.
EventLog Analyzer offers log management, file integrity monitoring, and real-time event correlation capabilities in a single console that help meeting SIEM needs, combat security attacks, and prevent data breaches.
Monitor critical changes to confidential files/folders with real-time alerts. Get detailed information such as 'who made the change, what was changed, when and from where' with predefined reports.
Centrally manage log data from sources across the network. Get predefined reports and real-time alerts that help meeting the security, compliance, and operational needs.
Centrally collect log data from Windows servers or workstations, Linux/Unix servers, network devices viz., routers, switches, & firewalls, and applications using agent less or agent based methods.
Perform in-depth forensic analysis to backtrack attacks and identify the root cause of incidents. Save search queries as alert profile to mitigate future threats.
Need Features? Tell Us
If you want to see additional features implemented in EventLog Analyzer, we would love to hear. Click here to continue