Store and manage your network logs from the cloud with ManageEngine Log360 Cloud.


A cloud-based SIEM solution provides SIEM functionalities as a service. Cloud SIEM solutions secure your network; provide threat intelligence; offer a console to detect, prioritize, and resolve security incidents; and help you comply with regulatory mandates―all from the cloud. Cloud SIEM solutions offer greater flexibility and ease of access when managing cybersecurity for both on-premises and cloud environments.
Log360 Cloud is ManageEngine's cloud-based SIEM solution that aims at providing comprehensive visibility and security management across both on-premises and cloud environments in a single platform.
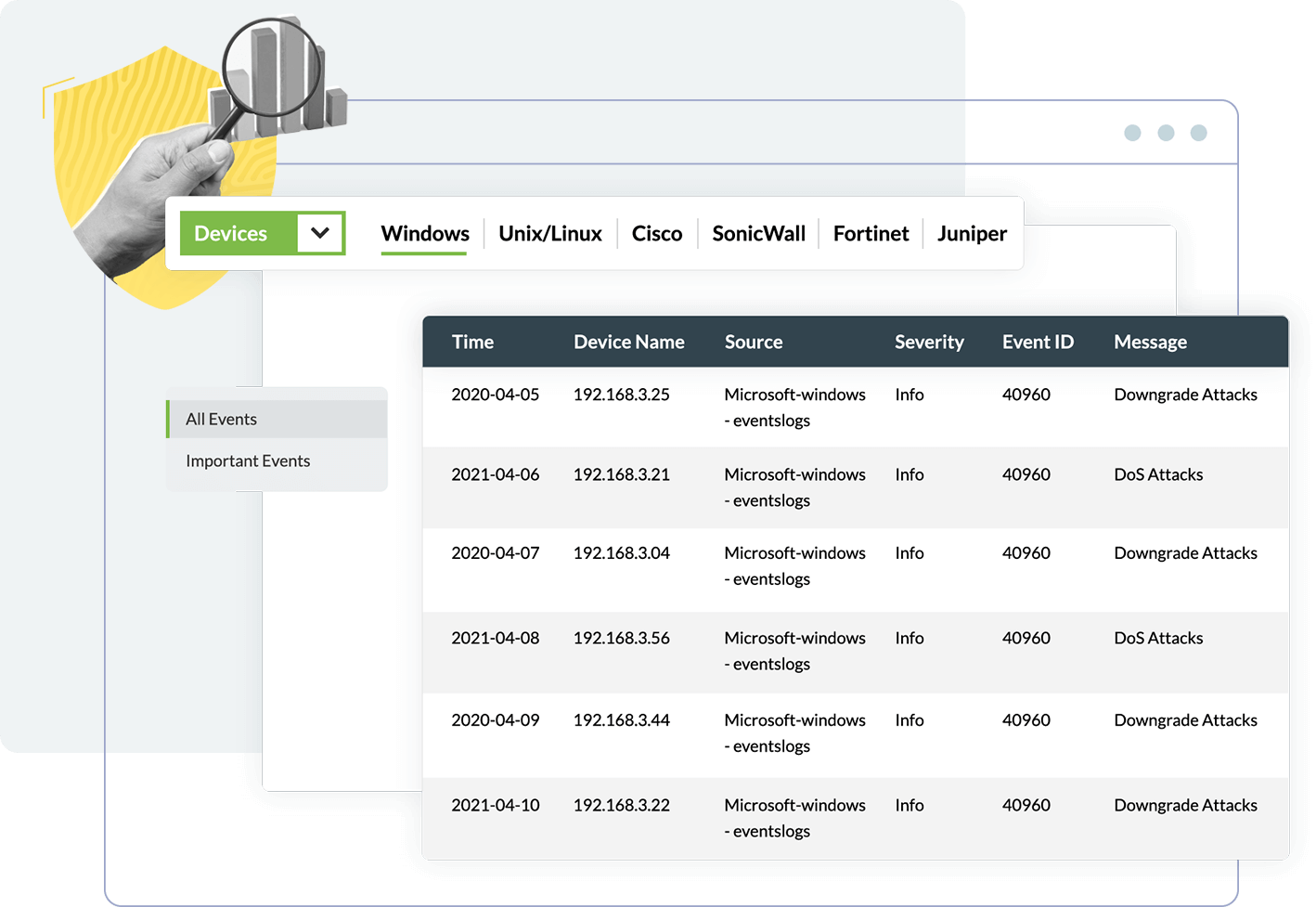
Log360 Cloud provides a comprehensive view of your network's security in real time with multiple auto-updated, graphical dashboards. Get complete visibility into your IT environment from anywhere with multiple security dashboards.
With Log360 Cloud, you can:
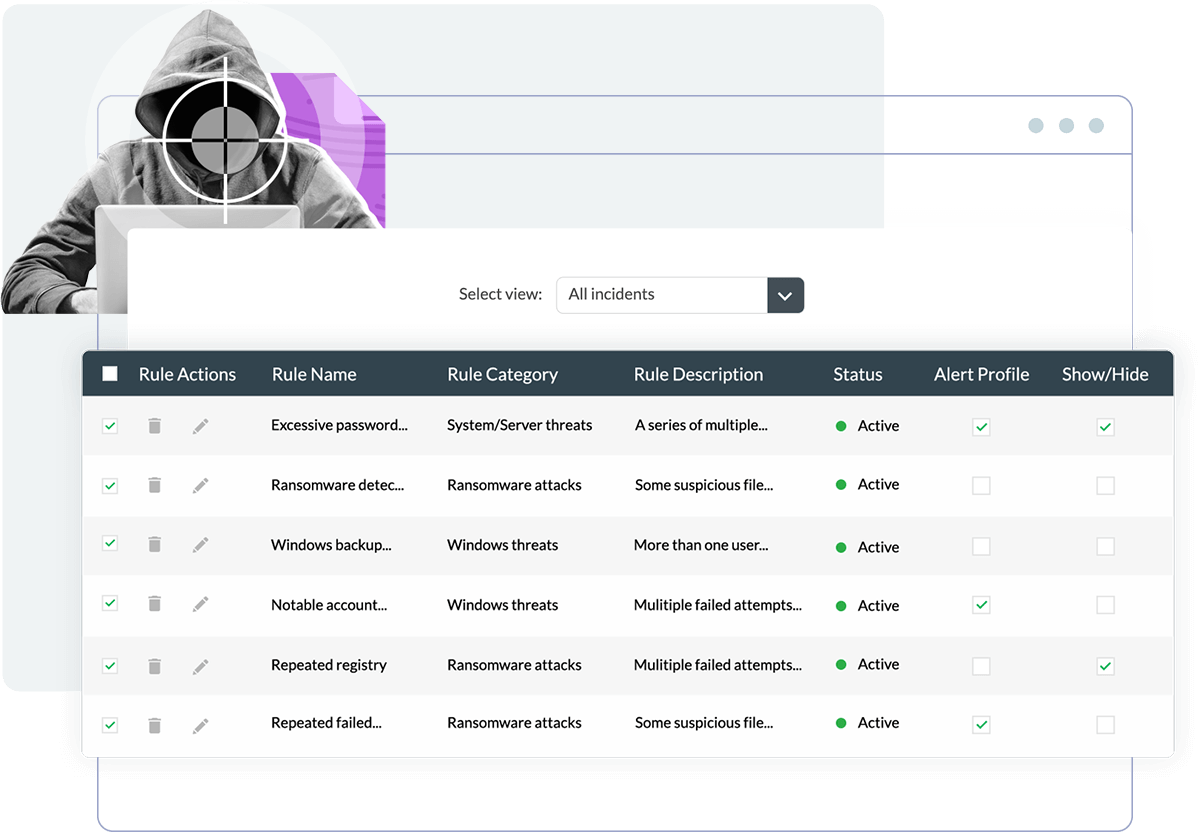
Rule-based threat detection is performed by applying a set of rules and observing if the events in the network match the rule criteria. This technique is well-known and widely used to detect known threats and indicators of compromise, such as brute-force attacks and ransomware attacks.
Log360 Cloud has a powerful correlation engine that lets you:
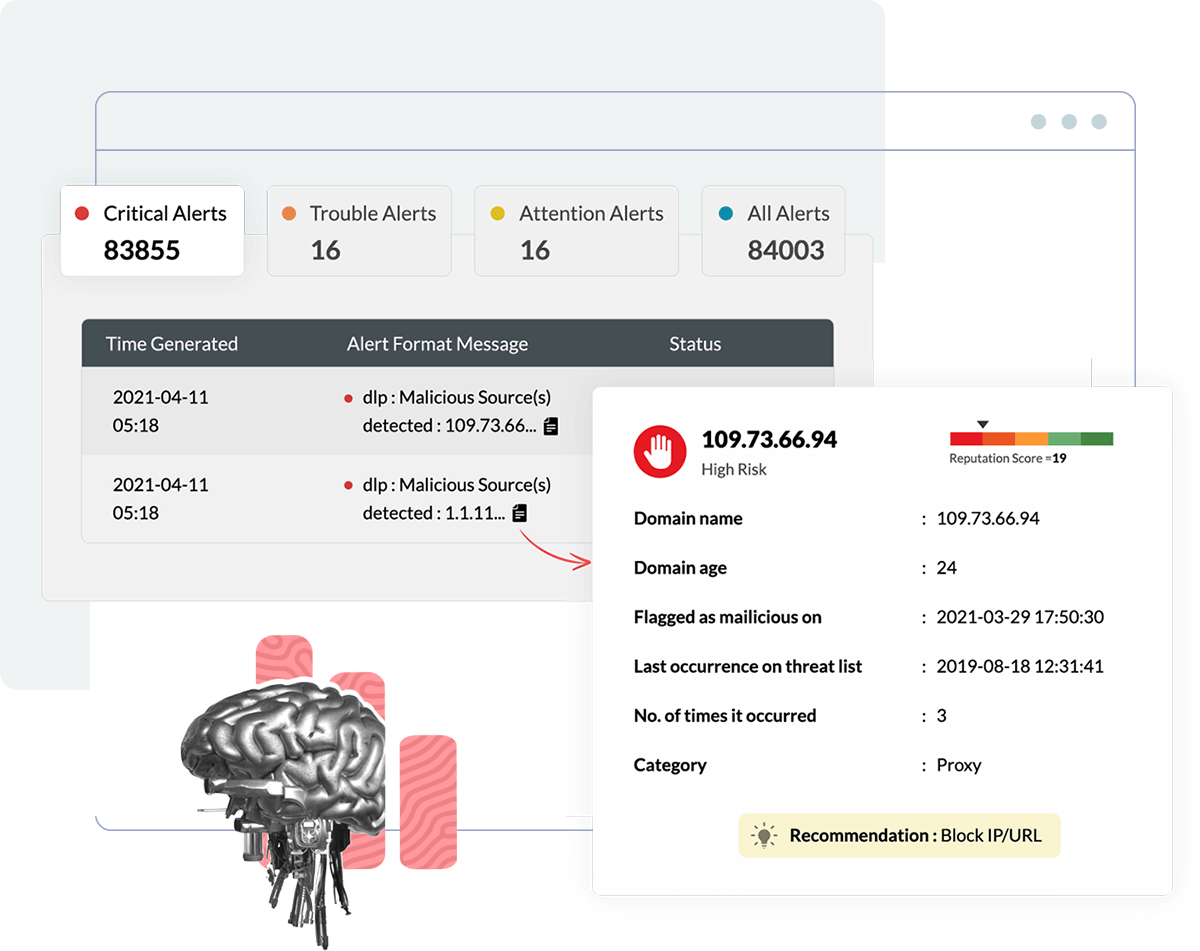
Threat intelligence is a repository of information on all known threats across the globe. With its ability to provide context to log data, threat intelligence enables organizations to decide on what indicators should be prioritized and what should be ignored.
Log360 Cloud comes with a fully configured threat intelligence module that auto-updates threat data from trusted open-source and commercial threat feeds. It also has an advanced threat analytics add-on that comes with a refined list of malicious IPs, URLs, and domains with reputation scores showing how severe the potential threat could be.
With Log360 Cloud, you can:
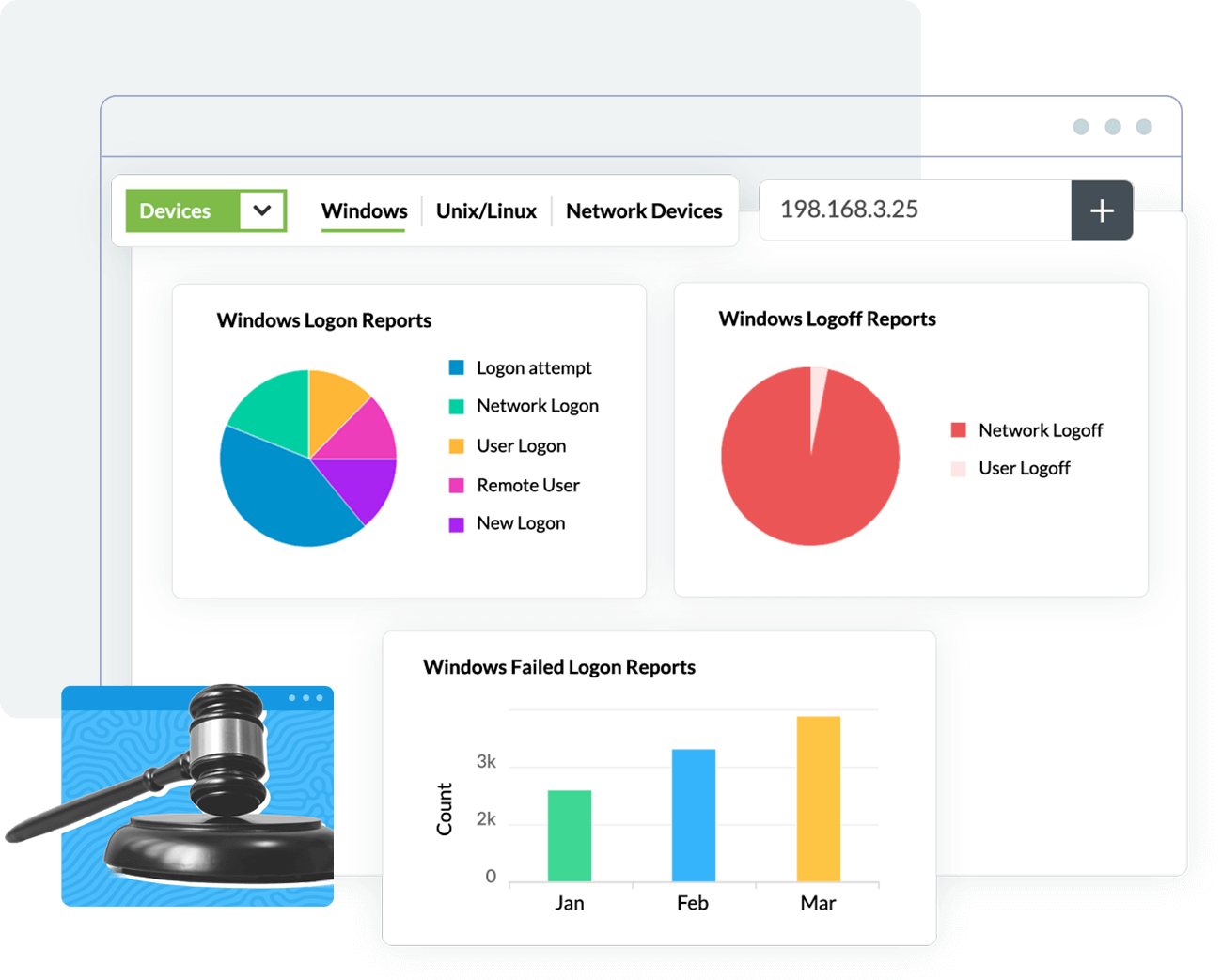
Organizations are often required to demonstrate adherence to various security standards and regulations during compliance audits by producing the corresponding reports, retaining log data over long periods, and monitoring for violations to ensure their business doesn't fall out of compliance.
A compliance management system helps do all of this, enabling you to be on top of your compliance game all the time. Log360 Cloud has an integrated compliance management system to help you meet compliance requirements for regulatory mandates such as PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001.
With Log360 Cloud, you can:
Enhance your security services with Log360 Cloud MSSP edition. Deploy centralized log management, threat analysis and compliance management at scale.
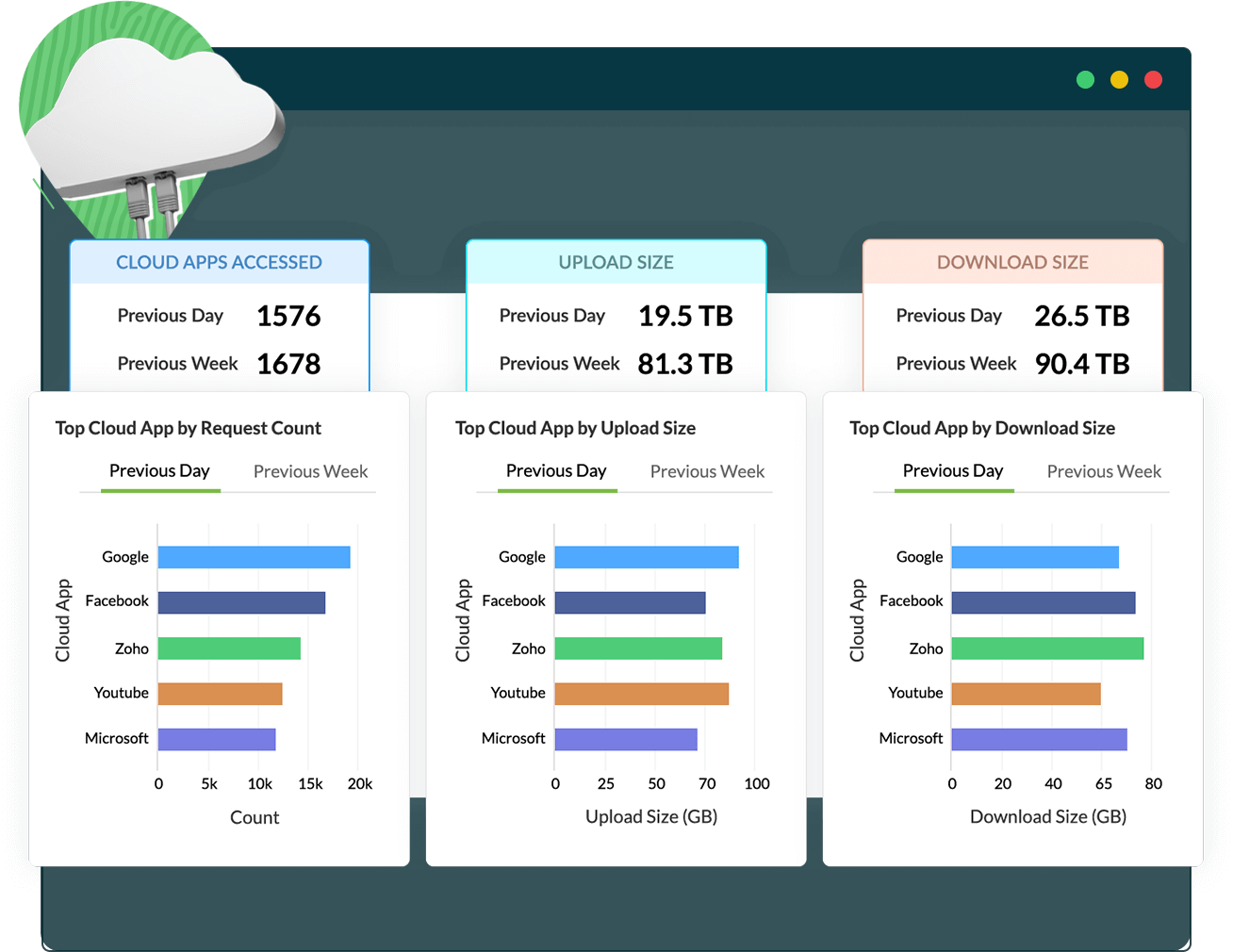
Try for freeMonitoring cloud application usage is necessary to regulate access to sensitive data in the cloud. Unsanctioned application usage, or shadow IT, reduces the visibility of user activity, making it easy for threat actors to sneak in their nefarious schemes comfortably.
A CASB equips you with the ability to discover shadow applications and their top users. With a cloud SIEM solution such as Log360 Cloud, this data can be used to build more context around the activities of threat actors, making it easy to detect malicious actions in your network.
With Log360 Cloud, you can:
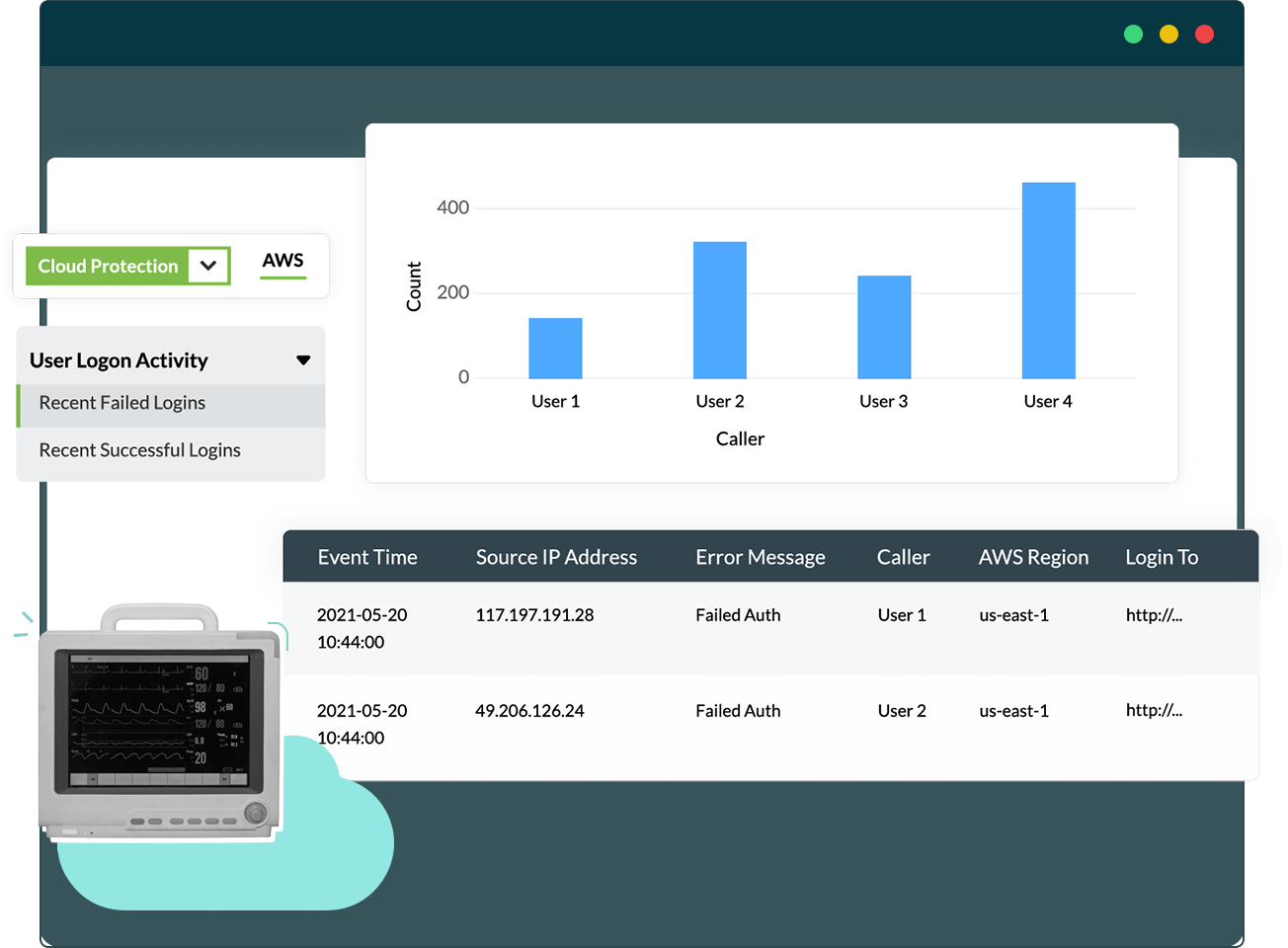
AWS CloudTrail logs, S3 server access logs, and Elastic Load Balancing (ELB) access logs record data access and contain details of each request, such as the request type, the resources specified in the request, the time and date the request was processed, the request path, and traffic volume. These logs are greatly valuable in understanding data access patterns, performing security audits, analyzing misconfiguration errors, and more.
Log360 Cloud supports agentless log collection for three types of AWS logs: AWS CloudTrail logs, AWS S3 logs, and ELB access logs. It also provides:
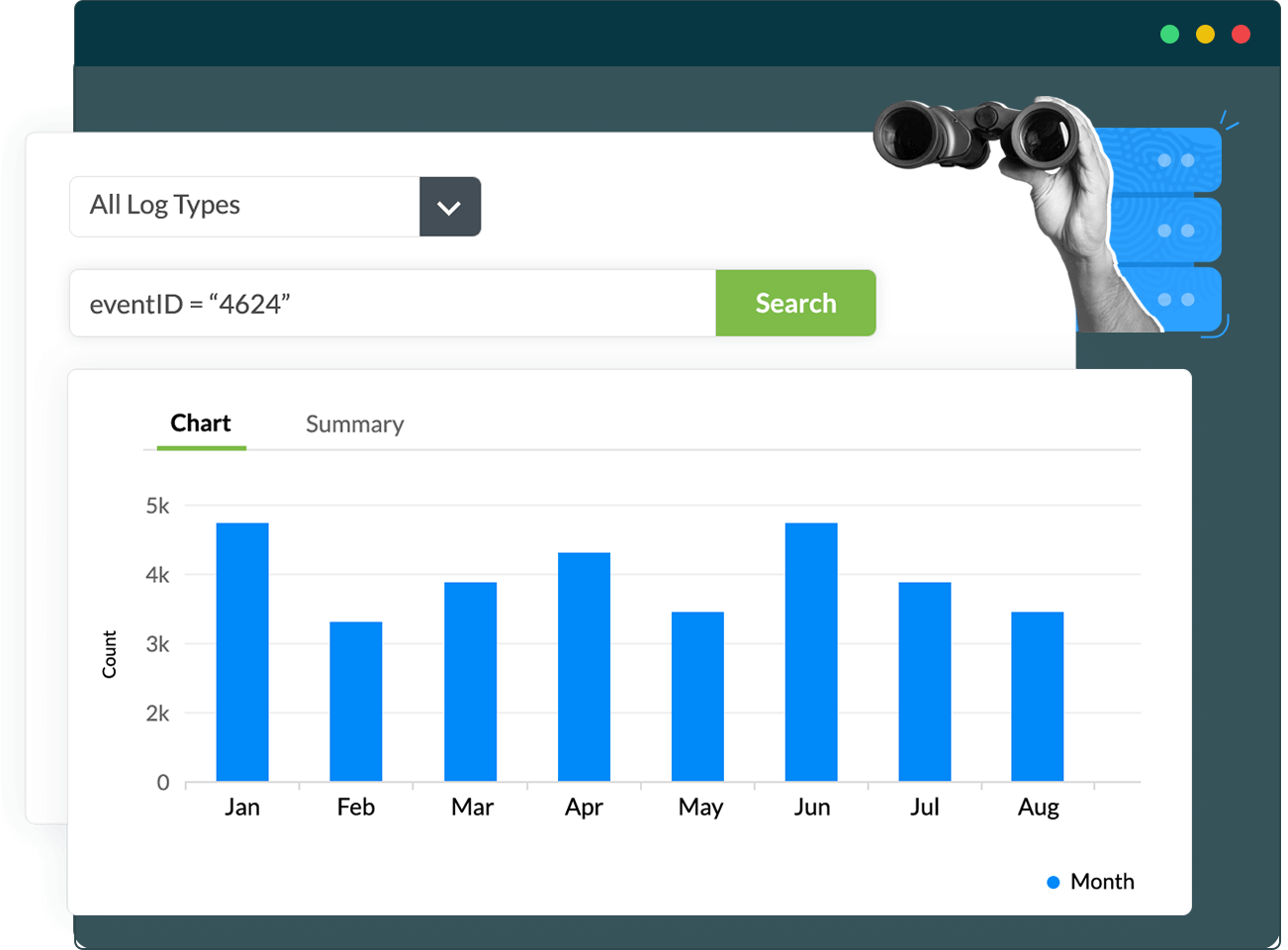
Aggregate logs from critical devices and securely store them on our cloud platform. Log360 Cloud lets you archive logs as required, for compliance and other purposes.
Log360 Cloud also has an intuitive and flexible search functionality that rapidly drills down into the raw logs and retrieves the results for your search query. The search criteria can consist of wild-cards, phrases, and Boolean operators. The security admin can search by event ID, severity, source, username, IP address, or combination of all to meet any search requirement.
Log360 Cloud lets you:
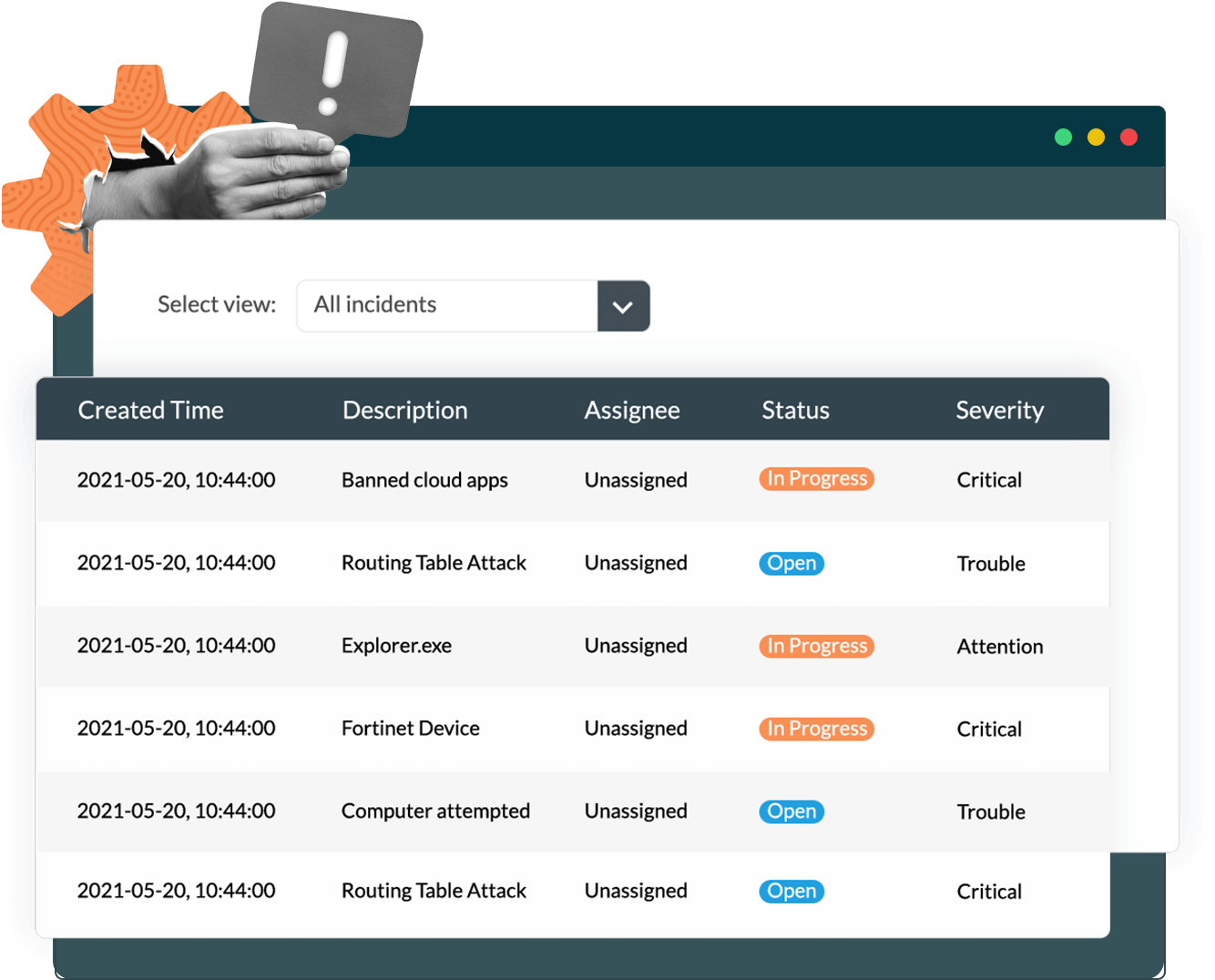
Incident management is the process of identifying, assigning, and resolving incidents In your network. Log360 Cloud's incident management capabilities ensure that you handle any security incident of interest methodically and with ease. Security administrators can assign incidents to technicians and track their progress. They can also automatically set up assignment rules to assign tickets for critical issues under their watch.
Log360 Cloud helps you speed up the incident resolution process. You can:
No credit card required.
For more than 20,000 GB (20 TB) storage, please contact our Sales team ( [email protected])